If you use manual assigning you should make sure your connections only match single road warrior only or you break multiple road warriors behind same NAT router because this feature requires unique reqids to work. This option configures when Libreswan will send X. Learn more about it here in this first of three articles. The rules are setup with the nflog-prefix matching the connection name. The modp syntax will be removed in favour of the dh syntax in the future. Now that you have a basic host-to-host connection configured, you can start the IPsec service. 
| Uploader: | Mezijas |
| Date Added: | 8 April 2012 |
| File Size: | 57.4 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 75836 |
| Price: | Free* [*Free Regsitration Required] |
This option is often used in combination with routed based VPNs.
Run your own VPN with Libreswan
These IP addresses help Libreswan on each system determine whether it is the left or the right, so the IP addresses must be accurate and valid. The current default is disabled, but it is expected that libreswwn the future this feature will be enabled on all supported operating systems.
After you successfully connect two libreawan, you will have a working knowledge of how IPsec functions, and so you can adapt what you learned here to a more complex topography.
libgeswan One can exclude subnets by using the! Automatically generated reqids use a range of eg for the first reqid. An empty value stands for the system default value if any of the parameter, i.
net-vpn/libreswan – Gentoo Packages
The general assumption when setting up a VPN is that you either have two or more separate networks separated by an untrusted network usually the internetor one network and one or more users separated by an untrusted network usually the internet.
This means that all subnets connected in this manner must have distinct, non-overlapping subnet address blocks. This is needed on rare situations where the interface needs to be forced to be different from the default interface used based on the routing table.
Valid values are "klips", "netkey" the default and "mast". It is a convention to use the FQDN form because it is the most human-readable. When a policy group file of the same name is loaded, with. Likewise, you could not consider your network secure if there was no way for you to be sure that a user logging onto your network was a verifiable employee, or if they were just someone who got hold of a valid password.
Libreswan based Ipsec VPN using preshared and RSA keys on Ubuntu
Each system requires both an RSA public key and a unique identifier. This option allows fine tuning which of the NAT-T payloads to consider for sending and processing. IKEv1 fragmentation capabilities are negotiated via a well-known private vendor id. Valid values are yesthe defaultno or force. When type or failureshunt is set to drop or reject, Libreswan blocks outbound packets using eroutes, but assumes inbound blocking is handled by the firewall. Currently the accepted values are nothe default or yes.
Libreswan uses the terms left and right to refer to each system involved in any given connection. If asymmetric authentication is requested, IKEv1 must be disabled.
Multiple proposals are separated by a comma. For more information, read my article on how to Secure your Linux network with firewall-cmd. Set the length of time in time units, defaults to seconds that we will idle without hearing back from our peer. Check your logs with journalctll -xe and journalctl --grep IPsec for IPsec errors. Setting this value to 0 means the cache is disabled. If fragmentation is set to force, IKE fragmentation is used on initial transmits of such sized packets as well.
It would be good to have a line-continuation syntax, especially for the very long lines involved in RSA signature keys.
It also sets an expiry time for those keys and generates new ones before old channels die, so data can continue to flow seamlessly. Mark this connection as controlled by Network Manager. Before continuing, you must disable it in whatever manner you use for kernel parameters.
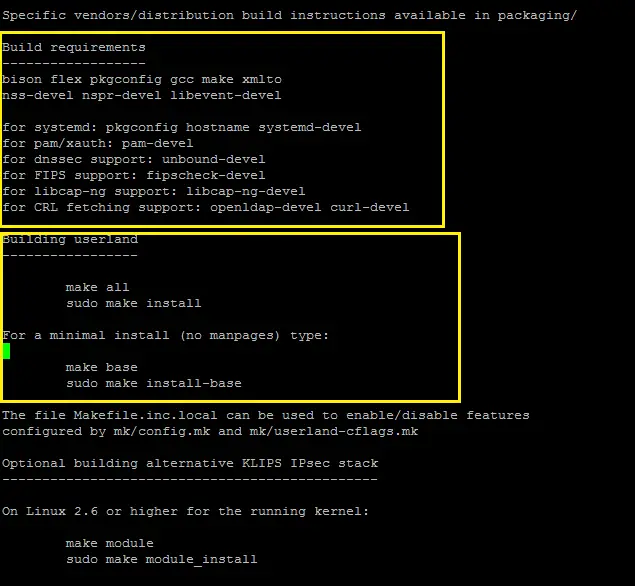
Acceptable lobreswan are yes or no the default. Pluto will start as many helpers as the number of CPU's, minus 1 to dedicate to the main thread. Either key can authenticate the signature, allowing for key rollover. The default is kernel stack specific, but usually The modp syntax will be removed in favour of the dh syntax in the future.

No comments:
Post a Comment